Please go through the following DMVPN and IPSec posts in order to understand the following configuration. I am using the same topology here and just configuring IPSec over it.
DMVPN Tunneling
IPSec over Static Virtual Tunnel Interface on Cisco IOS
For this example I am running DMVPN Phase 2 related configuration which is much more common.
Here also the R1 is the NHS / Hub and others are Clients / Spokes
DMVPN Config
R1(config)#interface Tunnel 0
R1(config-if)#ip address 192.168.123.1 255.255.255.0
R1(config-if)#ip nhrp authentication PASSWORD
R1(config-if)#ip nhrp network-id 1
R1(config-if)#tunnel source e0/0
R1(config-if)#tunnel mode gre multipoint
R2(config)#interface Tunnel0
R2(config-if)#ip address 192.168.123.2 255.255.255.0
R2(config-if)#ip nhrp authentication PASSWORD
R2(config-if)#ip nhrp map 192.168.123.1 13.18.12.1
R2(config-if)#ip nhrp network-id 1
R2(config-if)#ip nhrp nhs 192.168.123.1
R2(config-if)#tunnel source e0/0
R2(config-if)#tunnel mode gre multipoint
R3(config)#interface Tunnel0
R3(config-if)#ip address 192.168.123.3 255.255.255.0
R3(config-if)#ip nhrp authentication PASSWORD
R3(config-if)#ip nhrp map 192.168.123.1 13.18.12.1
R3(config-if)#ip nhrp network-id 1
R3(config-if)#ip nhrp nhs 192.168.123.1
R3(config-if)#tunnel source e0/0
R3(config-if)#tunnel mode gre multipoint
Now it's the time to run IPSec.
IPSec Config
This configuration is some what similar to using IPSec with Static Virtual Interface.
Configuring ISAKMP Policy..
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash md5
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
Configuring Key for ISAKMP sessions..
R1(config)#crypto isakmp key IPSEC-KEY address 0.0.0.0
Here 0.0.0.0 is used for any peer address..
Configuring IPSec Policy..
R1(config)#crypto ipsec transform-set TSET esp-aes esp-sha-hmac
R1(cfg-crypto-trans)#mode transport
Here, the Transport mode is used which will lower the overhead. Tunneling mode is not required here as DMVPN already tunnels it.
Configuring IPSec Profile..
R1(config)#crypto ipsec profile IPSEC_PROFILE
R1(ipsec-profile)#set transform-set TSET
Applying in tunnel interface..
R1(config)#int tunnel 0
R1(config-if)#tunnel protection ipsec profile IPSEC_PROFILE
Same IPSec configuration must be placed on Spoke routers too..
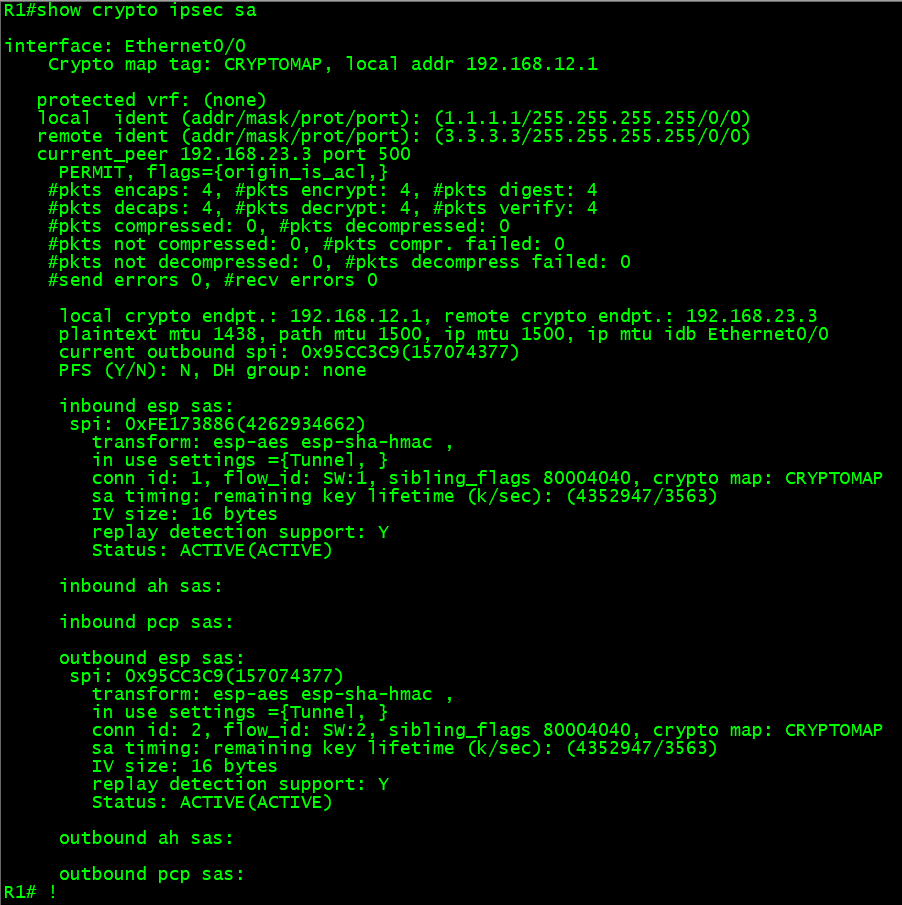
#show crypto ipsec sa will verify the implementation as usual..
DMVPN Tunneling
IPSec over Static Virtual Tunnel Interface on Cisco IOS
For this example I am running DMVPN Phase 2 related configuration which is much more common.
Here also the R1 is the NHS / Hub and others are Clients / Spokes
DMVPN Config
R1(config)#interface Tunnel 0
R1(config-if)#ip address 192.168.123.1 255.255.255.0
R1(config-if)#ip nhrp authentication PASSWORD
R1(config-if)#ip nhrp network-id 1
R1(config-if)#tunnel source e0/0
R1(config-if)#tunnel mode gre multipoint
R2(config)#interface Tunnel0
R2(config-if)#ip address 192.168.123.2 255.255.255.0
R2(config-if)#ip nhrp authentication PASSWORD
R2(config-if)#ip nhrp map 192.168.123.1 13.18.12.1
R2(config-if)#ip nhrp network-id 1
R2(config-if)#ip nhrp nhs 192.168.123.1
R2(config-if)#tunnel source e0/0
R2(config-if)#tunnel mode gre multipoint
R3(config)#interface Tunnel0
R3(config-if)#ip address 192.168.123.3 255.255.255.0
R3(config-if)#ip nhrp authentication PASSWORD
R3(config-if)#ip nhrp map 192.168.123.1 13.18.12.1
R3(config-if)#ip nhrp network-id 1
R3(config-if)#ip nhrp nhs 192.168.123.1
R3(config-if)#tunnel source e0/0
R3(config-if)#tunnel mode gre multipoint
Now it's the time to run IPSec.
IPSec Config
This configuration is some what similar to using IPSec with Static Virtual Interface.
Configuring ISAKMP Policy..
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash md5
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
Configuring Key for ISAKMP sessions..
R1(config)#crypto isakmp key IPSEC-KEY address 0.0.0.0
Here 0.0.0.0 is used for any peer address..
Configuring IPSec Policy..
R1(config)#crypto ipsec transform-set TSET esp-aes esp-sha-hmac
R1(cfg-crypto-trans)#mode transport
Here, the Transport mode is used which will lower the overhead. Tunneling mode is not required here as DMVPN already tunnels it.
Configuring IPSec Profile..
R1(config)#crypto ipsec profile IPSEC_PROFILE
R1(ipsec-profile)#set transform-set TSET
Applying in tunnel interface..
R1(config)#int tunnel 0
R1(config-if)#tunnel protection ipsec profile IPSEC_PROFILE
Same IPSec configuration must be placed on Spoke routers too..
#show crypto ipsec sa will verify the implementation as usual..